Secondary Computing Cybersecurity
Abonnement erforderlich
10.000+ Ergebnisse für 'secondary computing cybersecurity'

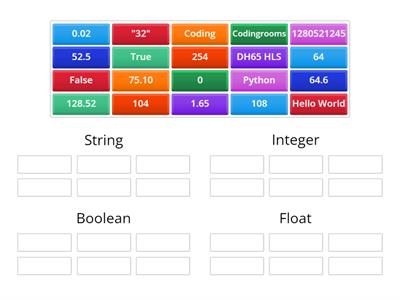
Cybersecurity Words
It's a Match

Cybersecurity
It's a Match

Hack The Game
Die richtige Reihenfolge

Cybersecurity Threats
Die passende Antwort

Cybersecurity Acronyms
It's a Match

CyberSecurity - A1
Öffnen Sie die Box

Avatars
Vervollständige den Satz

Secondary Storage
Hau den Maulwurf

Cybersecurity
Quiz

Cybersecurity
Quiz
Primary and Secondary Data
Die passende Antwort

Cybersecurity
Anagramm

Features of Secondary Storage
It's a Match

CTG Cybersecurity
Anagramm
Cybersecurity, network security and data transfer
Geschwindigkeitssortierung

Secondary Storage- train
Luftballons

cybersecurity
Anagramm

CYBERSECURITY
It's a Match

Cybersecurity Quiz
Quiz

Cybersecurity Wordsearch
Wörtersuche

CyberSecurity Crossword
Kreuzworträtsel

Cybersecurity
Jagd durchs Labyrinth

Cybersecurity
Vervollständige den Satz

Hangman - Cybersecurity
Galgenmännchen

Safe to share online?
Die richtige Gruppe

Whack the correct variable names
Hau den Maulwurf

Bussiness ethics
Jagd durchs Labyrinth

carliandro
It's a Match

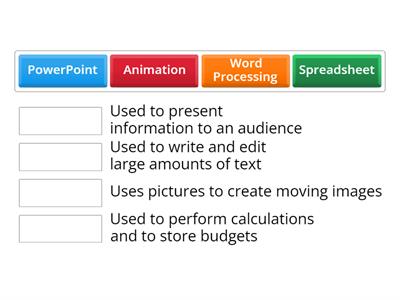
S1 Computing - Computer Hardware
Beschriftetes Diagramm

SDD Flowchart
Beschriftetes Diagramm

WDD layouts
Beschriftetes Diagramm

WDD Wireframes to code
Beschriftetes Diagramm

National 5 Revision
Glücksrad