Secondary Computing Cybersecurity
Nepieciešams abonements
Rezultātu skaits vaicājumam "secondary computing cybersecurity": 10 000+

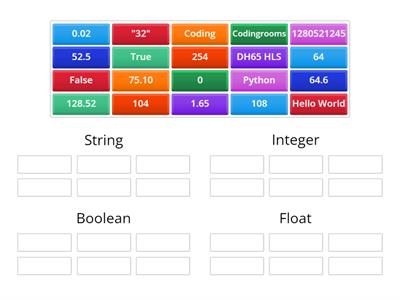
Cybersecurity Words
Saderību meklēšana

Cybersecurity
Saderību meklēšana

Hack The Game
Kārtošana pēc pozīcijas

Cybersecurity Threats
Atrast saderības

Cybersecurity Acronyms
Saderību meklēšana

CyberSecurity - A1
Atveriet kastīti

Avatars
Pabeidziet teikumu

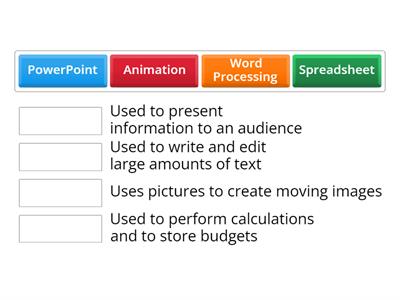
Secondary Storage
Trāpiet kurmim

Cybersecurity
Viktorīna

Cybersecurity Think Quiz
Viktorīna

Cybersecurity
Viktorīna
Primary and Secondary Data
Atrast saderības

Cybersecurity
Anagramma

Features of Secondary Storage
Saderību meklēšana

CTG Cybersecurity
Anagramma
Cybersecurity, network security and data transfer
Ātruma šķirošana

Secondary Storage- train
Balonu pārduršana

Cybersecurity Aeroplane Key Word Game
Lidmašīna

cybersecurity
Anagramma

CYBERSECURITY
Saderību meklēšana

Cybersecurity Quiz
Viktorīna

Cybersecurity Wordsearch
Vārdu meklēšana

CyberSecurity Crossword
Krustvārdu mīkla

Cybersecurity
Pakaļdzīšanās labirintā

Cybersecurity
Pabeidziet teikumu

Hangman - Cybersecurity
Karātavas

Safe to share online?
Kārtošana grupās

Whack the correct variable names
Trāpiet kurmim

Bussiness ethics
Pakaļdzīšanās labirintā

carliandro
Saderību meklēšana

S1 Computing - Computer Hardware
Diagramma ar etiķetēm

SDD Flowchart
Diagramma ar etiķetēm

WDD layouts
Diagramma ar etiķetēm

WDD Wireframes to code
Diagramma ar etiķetēm

National 5 Revision
Nejaušības ritenis