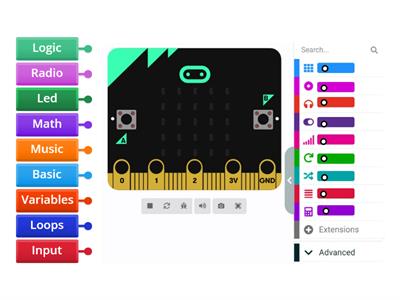
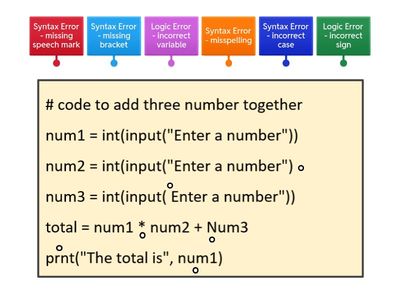
Secondary Computing Cybersecurity
Abonnement kreves
10 000+ resultater for secondary computing cybersecurity

Cybersecurity Words
Match opp

Cybersecurity
Match opp

Hack The Game
Rangeringsrekkefølge

Cybersecurity Threats
Finn treffet

Cybersecurity Acronyms
Match opp

CyberSecurity - A1
Åpne boksen

Avatars
Fullfør setningen

Secondary Storage
Whack-a-mole

Cybersecurity
Spørrelek

Cybersecurity Think Quiz
Spørrelek

Cybersecurity
Spørrelek
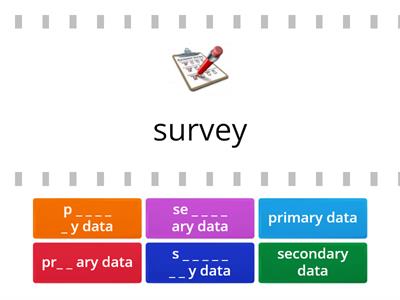
Primary and Secondary Data
Finn treffet

Cybersecurity
Anagram

Features of Secondary Storage
Match opp

CTG Cybersecurity
Anagram
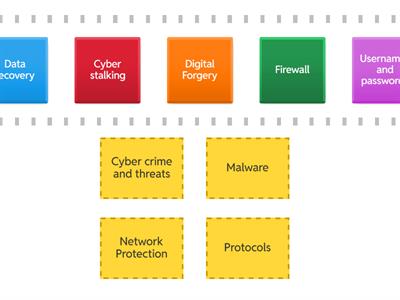
Cybersecurity, network security and data transfer
Rask sortering

Secondary Storage- train
Ballong pop

cybersecurity
Anagram

CYBERSECURITY
Match opp

Cybersecurity Quiz
Spørrelek

Cybersecurity Wordsearch
Wordsearch

CyberSecurity Crossword
Kryssord

Cybersecurity
Labyrintjakt

Cybersecurity
Fullfør setningen

Hangman - Cybersecurity
Bøddel

Safe to share online?
Gruppe sortering

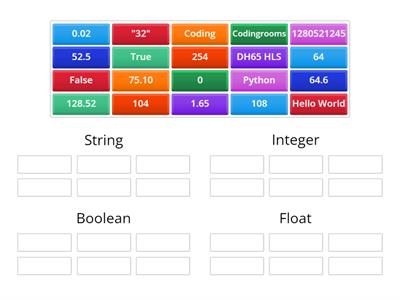
Whack the correct variable names
Whack-a-mole

Bussiness ethics
Labyrintjakt

carliandro
Match opp

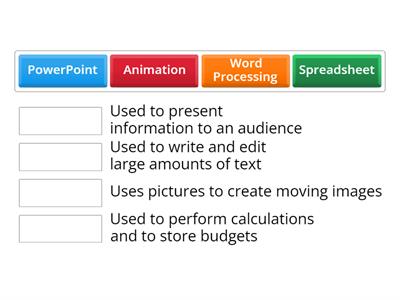
S1 Computing - Computer Hardware
Merket diagram

SDD Flowchart
Merket diagram

WDD layouts
Merket diagram

WDD Wireframes to code
Merket diagram

National 5 Revision
Tilfeldig hjul