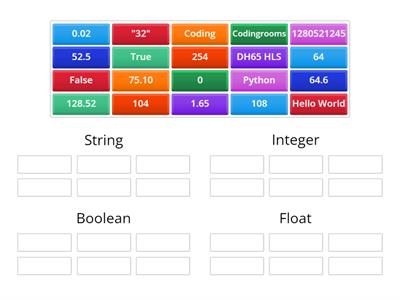
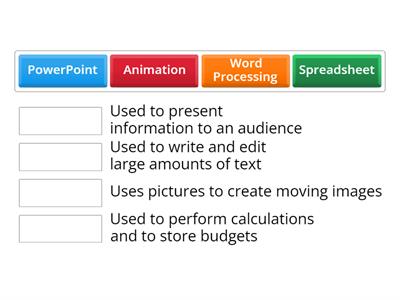
Secondary Computing Cybersecurity
Wymagana subskrypcja
Liczba wyników dla zapytania „secondary computing cybersecurity”: 10 000+

Cybersecurity Words
Połącz w pary

Cybersecurity
Połącz w pary

Hack The Game
Ustaw w kolejności

Cybersecurity Threats
Znajdź parę

Cybersecurity Acronyms
Połącz w pary

CyberSecurity - A1
Odkryj karty

Avatars
Uzupełnij zdanie

Secondary Storage
O rety! Krety!

Cybersecurity
Test

Cybersecurity
Test
Primary and Secondary Data
Znajdź parę

Cybersecurity
Anagram

Features of Secondary Storage
Połącz w pary

CTG Cybersecurity
Anagram
Cybersecurity, network security and data transfer
Szybkie sortowanie

Secondary Storage- train
Przebij balon

cybersecurity
Anagram

CYBERSECURITY
Połącz w pary

Cybersecurity Quiz
Test

Cybersecurity Wordsearch
Znajdź słowo

CyberSecurity Crossword
Krzyżówka

Cybersecurity
Labirynt

Cybersecurity
Uzupełnij zdanie

Hangman - Cybersecurity
Wisielec

Safe to share online?
Posortuj

Whack the correct variable names
O rety! Krety!

Bussiness ethics
Labirynt

carliandro
Połącz w pary

S1 Computing - Computer Hardware
Rysunek z opisami

SDD Flowchart
Rysunek z opisami

WDD layouts
Rysunek z opisami

WDD Wireframes to code
Rysunek z opisami

National 5 Revision
Koło fortuny