High School Computer Science Cybersecurity
Wymagana subskrypcja
Liczba wyników dla zapytania „high cs cybersecurity”: 10 000+
cybersecurity
Test
Cybersecurity Spinner Game!
Koło fortuny

Cybersecurity Vocabulary
Połącz w pary
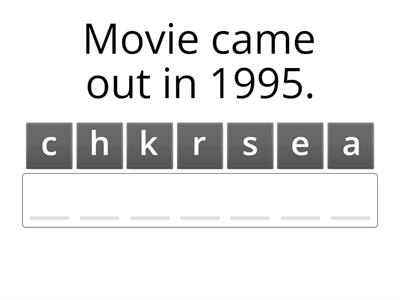
Cybersecurity
Anagram

Password Safe Tea
Posortuj

Cybersecurity
Anagram

Cybersecurity
Anagram

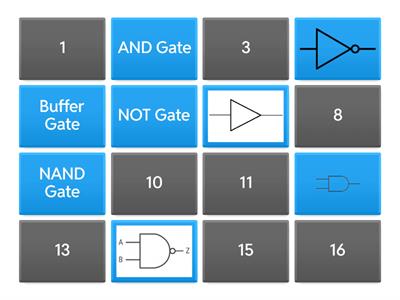
LOGIC GATE TILES
Odwracanie kart

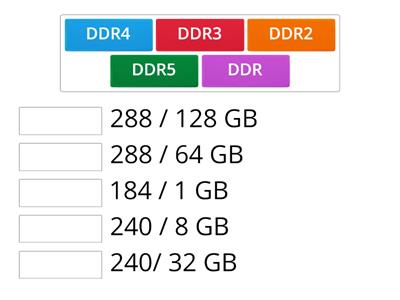
Dell LCD Screen
Rysunek z opisami

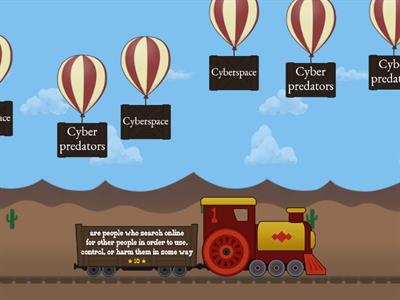
Game Design
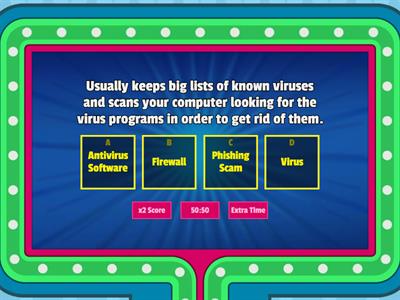
Teleturniej

Cybersecurity
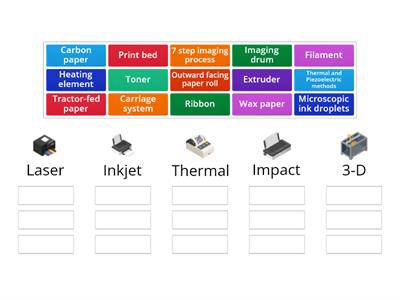
Posortuj

Cybersecurity
Fiszki

Cybersecurity
Losowe karty

Unit 6- Array
Odkryj karty

Веб-дизайн кольорові моделі
O rety! Krety!
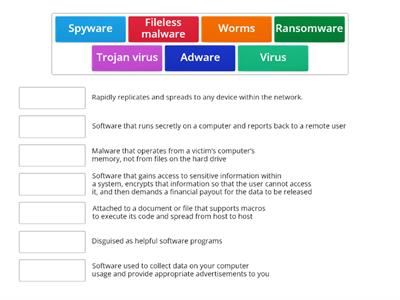
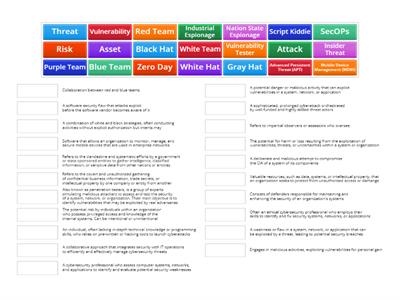
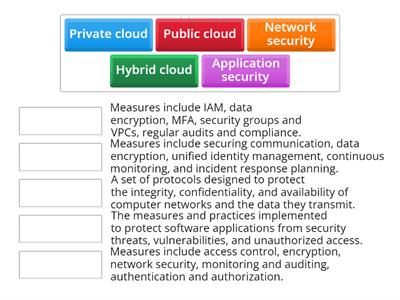
Cyber Security
Połącz w pary

Video Game HUD (Interface)
Rysunek z opisami
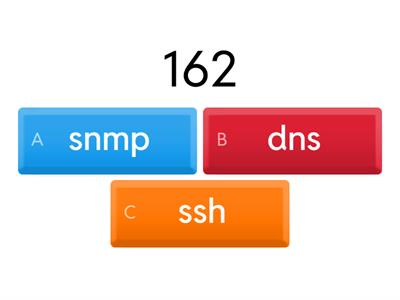
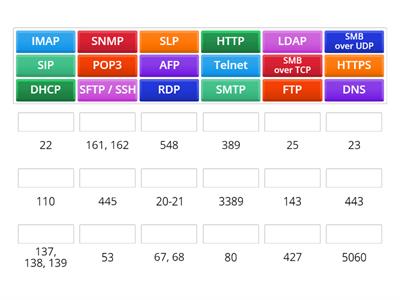
Ports
Test

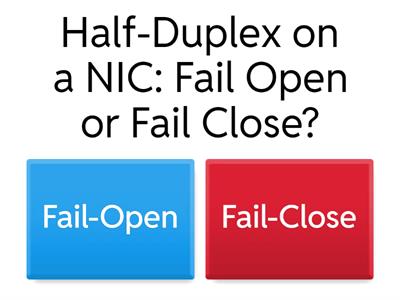
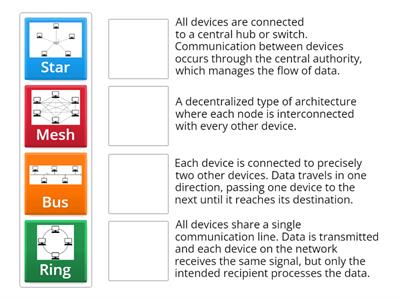
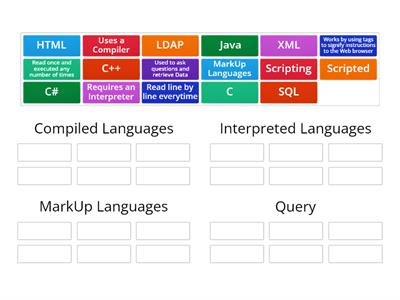
Networking+
Połącz w pary

Digital Technology Foundation Terms
Teleturniej

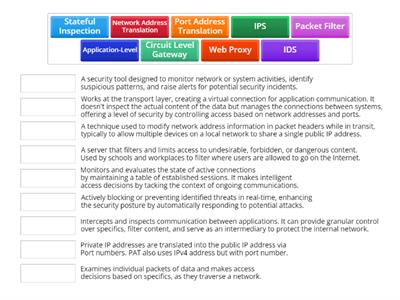
overview security
Połącz w pary

AR NOOR
Koło fortuny
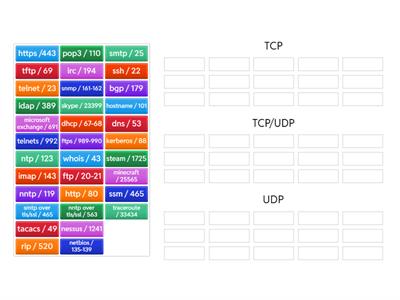
Ports and Protocols
Posortuj
OSI Model
Posortuj

Digital Literacy Midterm Review
Znajdź parę

CS
Połącz w pary

CS
Fiszki

CS Wordsearch
Znajdź słowo