Secondary Computing Cybersecurity
Obuna talab etiladi
10 000+ natijalari 'secondary computing cybersecurity'

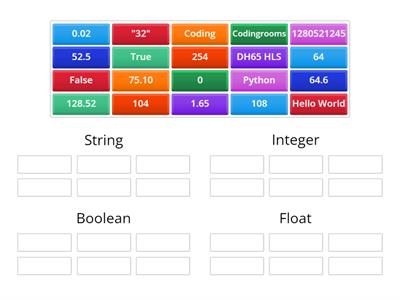
Cybersecurity Words
Tenglashtirish

Cybersecurity
Tenglashtirish

Hack The Game
Tartib tartibi

Cybersecurity Threats
Oʻyinni qidirish

Cybersecurity Acronyms
Tenglashtirish

CyberSecurity - A1
Oynani ochish

Avatars
Gapni bajarish

Secondary Storage
Whack-a-mole

Cybersecurity
Viktorina

Cybersecurity Think Quiz
Viktorina

Cybersecurity
Viktorina
Primary and Secondary Data
Oʻyinni qidirish

Cybersecurity
Anagramma

Features of Secondary Storage
Tenglashtirish

CTG Cybersecurity
Anagramma
Cybersecurity, network security and data transfer
Tezlik bilan saralash

Secondary Storage- train
Balon pop

cybersecurity
Anagramma

CYBERSECURITY
Tenglashtirish

Cybersecurity Quiz
Viktorina

Cybersecurity Wordsearch
So'zlarni qidirish

CyberSecurity Crossword
Krossword

Cybersecurity
Labirent quvish

Cybersecurity
Gapni bajarish

Hangman - Cybersecurity
Askar

Safe to share online?
Guruh saralash

Whack the correct variable names
Whack-a-mole

Bussiness ethics
Labirent quvish

carliandro
Tenglashtirish

S1 Computing - Computer Hardware
Etiketli diagramma

SDD Flowchart
Etiketli diagramma

WDD layouts
Etiketli diagramma

WDD Wireframes to code
Etiketli diagramma

National 5 Revision
Gʻildirakni aylantirish